If somebody borrows or uses your computer, they can find out what your IP address is in seconds, as there are countless free websites that let you do that.From an email. If you send an email to someone, they can check the header of the message, which could contain your IP address. Yahoo! and Microsoft Outlook are known to include IP addresses in the email header.Clicking on a link.
Any link you click on will need to provide your iP address for the server at the other end to deliver the content provided by the link. Whoever owns that server will see your IP address.By hacking your router. If somebody has guessed your router's password and logged in, they can easily view your IP address.From a web server. Every time you visit a website, your IP address is collected and stored on a server.
Anyone who owns that server can go and look up your IP.Clicking on an ad. When you click on an ad, you're giving your IP to the service provider. Some online ads can be created by malicious actors and put your security at risk.Participating in online forums. Hackers can set a fake hotspot and view your IP address and personal information or even infect your device with malware.On social networks. While using social media is fun, these platforms collect a lot of sensitive information about your life, friends, habits, interests, and your IP. If you are hosting a java server than you only need TCP afaik unless they added udp support.
If you are concerned about security then you should follow basic network security protocols. Only foward the ports and protocls needed specifically to the internal server, nothing more. Create a seperate RFC1918 internal lan (/30) on its own vlan and create acls to prevent it from talking to anything but what it needs to. For these required open ports you can further secure them by using IP blocklists, Geoblock lists, IPS, packet scrubbing, etc. However this is all pretty overkill and requires powerful firewall software and in general as long as the minecraft server is configured correctly and patched I wouldnt worry too much. It is best to have a deticated device doing it running like mineOS or something that has built in security/firewall.
Just make sure nothing else on your network can get the IP of your server and that its set up right. Also remember if you are on a home connection chances are high your IP will be dynamic, so it could change causing you problems. Lastly make sure you are taking backups of your server lest someone log on and blow everything up. You can use whitelists to only allow trusted people but in general its a pain to manage. State highways are always going to be open unless theres a major dissaster.
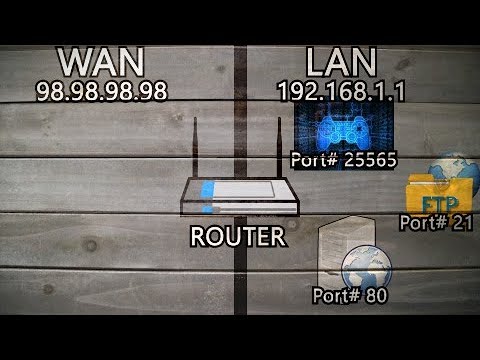
Same thing with ports there different roads to communicate. You wouldnt have all traffic running on one road so you wouldnt on a port either. Port forwarding is opening a port for a specific ip usually.
In your router settings you need to specify a name for your port forward an ip address to port forward and the port/s. Now to hide your ip in this process you will need to find some software or write your own code that will make your exploit look to a dns server and when it finds that server it will update the ip. So if you wrote a reverse tcp in ruby like the ones metasploit uses i think... Its best you do some reaserch in most cases for exploit building no one will help you unless your a close friend who they know and trust. If you would like some more info on the matter im sure google will help with a few key words picked from this mesage.
Of course yould want to connect to a vpn or maybe even a multi hop vpn to make it harder to be traced. Just remember the long your connected the easier it is for them to find you. In such a case, users mostly don't see the need to set a password for convenience, thinking that malicious actors won't guess their passwords. Unfortunately, although this enables your friends to access the game quickly, so do hackers. As hackers test multiple passwords per second to access devices, they also attack open protocols like games on internet-connected devices. So, create a strong password and update your device's operating system regularly to prevent this issue.
Port forwarding lets people connect to the mapped port on whatever device you've pointed it at. The security rests solely with whatever software on that device is listening on that port. So say you've port forwarded to remote desktop on a PC you never update. Odds are it will be easy to get in to that, and then to whatever it has access to (maybe the whole LAN including the "secure" side of the router). On the other hand, if you port forwarded 6789 to port 22 on a Linux box you update every night, chances are very slim anyone will be able to break-in to it. But if you had no ports open, there is nowhere to connect and try and break into.
Some routers may have intrusion-detection features, but they may not be able to do things like decide if remote user X is you or a hacker trying to get to the forwarded port. This is an important security measure whether you have a baby monitor or not. Be sure to keep your router's firmware updated, disable remote router access if you changed the default setting, and create a strong WiFi password. Never leave your WiFi network open—keeping it password protected significantly reduces the chance of a hacker gaining access to your network. Using PureVPN for forwarding ports is safe because you are building a secure internet connection between two devices with an added security layer. Plus, you can encrypt internet traffic with a VPN connection on your network, and hackers won't easily penetrate the devices.
Also, you can install games and torrents faster with a VPN connection as they offer P2P servers. The open port that resides at the global public IP address where the VPN is hosted is the root cause of the current security dilemma. A VPN server by definition must reside at a routable global IP address and provide an open port where legitimate users can initiate a connection and log in with their username and password. The problem is that open ports are also vulnerable to unsolicited inbound traffic.
Parents today have more access than ever to tech-based tools that help them care for their children. But as modern technology continues to evolve, the risk of hacking and security vulnerabilities goes up. Anything that's connected to the internet is an opportunity for cybercriminals to access your data, and unfortunately, that includes baby monitors. When running a remote access connection, the password you use will determine your computer's security level. Unfortunately, hackers are running numerous passwords per second, trying to access every device connected to the internet.
The best way to eliminate this weakness is by using a strong password or key-based authentication. Port forwarding allows external computers to connect to your computer within a private network. This does sound secure because you are configuring the router and feeding it a specific port number. Port forwarding a security camera or computer is also safe but has low reliability.
Your computer is safe from external threats while port forwarding if you are using Windows Vista, Windows 7, 8, or 10. They have in-built firewalls for safe port forwarding. The idea behind UPnP was to allow internet-based apps and devices to create port forwarding rules on your router automatically to allow outside traffic.
For instance, UPnP may automatically open ports and forward traffic for a device running a game server without the need to manually configure access in your router settings. Thanks to integrated network firewalls, your network is in the same position. You can access other online services, such as websites or game servers, but other internet users can't access your devices in return. The drawbridge is raised, as your firewall actively blocks any attempts from outside connections to breach your network.
As outlined above, WiFi baby monitors are susceptible to hackers if your network is unsecured or a hacker finds a way to bypass your passwords. Port forwarding inherently gives people outside of your network more access to your computer. Network access translation , the technology that allows multiple devices to share one IP address, normally also protects your devices from external attacks. I am sure there is something else going on here and I feel confident the cameras had nothing to do with the DNS being changed. I have been dealing with this stuff since 1991 and I have never seen this be the cause of cameras.
Also what are you using for real-time virus & malware scanning? You need to have both or your at risk of something happening. Also u mentioned google DNS servers, Do you have Virus & Malware scanning at the edge of your network aka your gateway/router? You should consider changing you client DNS setting to something with more filtering then GoogleDNS provides like OpenDNS, Symantec or many others.
Can you get hacked through port forwarding I suggest OpenDNS because it gives a nice balance of security and performance. If a computer tries to connect to your device when the NAT firewall is active, the connection is jammed or discarded. However, port forwarding lets unsolicited connections pass through the NAT firewall on particular ports. As a result, devices on the internet can launch connections and access any service.
For instance, other users on a P2P network can download a file from your device. Bugs, malware, and phishing can easily allow cybercriminals and hackers to infiltrate internet-accessible devices and expose sensitive information on devices connected to the breached network. Fraud, blackmail, identity theft, and denial of services are often the result of these attacks, leaving consumers and vendors with severe losses. Like all other phone systems or network connected devices, the NEC phone system can be a potential target for hackers. If you're only using your baby monitor to share audio and video signals within the perimeter of your private WiFi network, a hacker would first need to get access to your home router. They will only then try to access all the devices that use that router to connect to the internet .
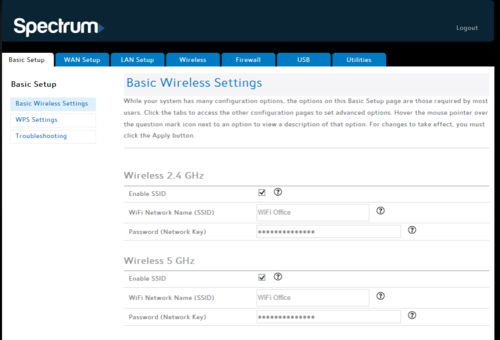
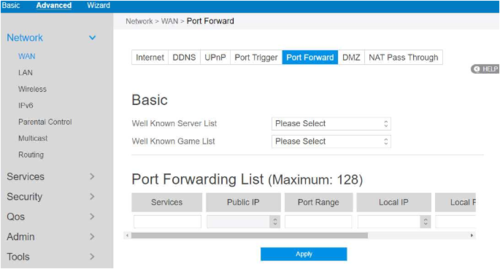
Port forwarding is a process on local network routers that forwards connection attempts from online devices to specific devices on a local network. This is thanks to the port forwarding rules on your network router that match the connection attempts made to the correct port and IP address of a device on your network. Our web ports might be open, but your home router's ports shouldn't be, as this opens a hole for malicious hackers. However, you may need to allow access to your devices over the internet using port forwarding from time to time. To help you learn more about port forwarding, here's what you'll need to know. I can't comment on the missing videos but I can't overstate how risky port forwarding can be when used with an IoT device like the Arlo SmartHub.
You're relying on the hub and many other devices on your network being perfectly secure, un-hackable, which is a thing that does not exist. I'm not saying the hub isn't secure, I'm saying that to enable port forwarding to any IoT device is to bet that no hacker will ever find a way to exploit that configuration. If I had to choose between taking that risk for the years that the hub will be in operation or paying for a router with VPN capability, I'd go with the VPN option. Remote.it was created by networking industry veterans seeking to solve the persistent security problems related to port forwarding and global IP addresses. To make a long story short, there are some risks of port forwarding. If you are opening ports, then you are opening direct lines for hackers and malware attacks in a way.
That's why you must take safety precautions when you are port forwarding devices. This is where a VPN, or Virtual Private Network, becomes helpful. A port scan of the network can reveal that it is open on the nondefault ports. This could then be exploited to gain access to the device that the ports arw forwarded to, in this case an nvr which has any number of cameras attached to it.
If the VPN has a NAT firewall, then it should offer port forwarding as a feature. Unfortunately, there are only a handful of VPN services that support port forwarding. Usually, you can set it up in the account settings on the website or the app.
Also, note that port forwarding may not be working on specific servers. Port forwarding enables incoming internet connections to get to specific programs and devices on a private network. Keep in mind that the private network can comprise devices connected to a router or users to a VPN. That's why you must take safety precautions when you are port forwarding devices. Whether you have heard about port forwarding or not, we will try to answer this question in simpler words.
Port Forwarding allows computers over the internet to connect to a computer or server within a private home network. This makes your computer accessible to another computer through your network, which is being used to filter traffic to multiple devices on your network. But through port forwarding, you specify that your PC gets traffic to certain ports of your choosing, and your Xbox gets traffic to other ports, and the list goes on. In the traditional sense, the functionality of router is routing the packets among the networks. The security threat at this layer is due to the additional functionality the routers provide. In addition to providing routing, the routers provide configurations such as default DNS server addresses to the devices connecting to it.
A malicious DNS server can navigate the victims to phishing sites and exploit users. Your home's Wi-Fi router is your gateway to a seamless and faster internet connection. But an unsecured Wi-Fi router can create the perfect avenue for hackers to access your home's wireless systems and cause havoc. Regardless, even with millions of cyber-attacks daily on the internet, the Eero router may be the solution to the continued security vulnerability in homes today.
Iodine lets you tunnel IPv4 data through a DNS server. It creates a network interface on each of the clients and connects them together as if they shared the same network. This feature is unique to Iodine since other DNS tunneling tools focus on tunneling specific ports, and not the entire IPv4 traffic. This allows computers to ping each other, access all UDP/TCP ports and all other protocols that are encapsulated by an IP header. Most organizations have a firewall that acts as a filter between their sensitive internal networks and the threatening global Internet.
But it continues to cost companies and has seen hackers invest more time and effort developing tools. A recent study found that DNS attacks in the UK alone have risen 105% in the past year. DNS tunneling is attractive–hackers can get any data in and out of your internal network while bypassing most firewalls. Here's everything you need to know about the attack, the tools and how to stop it.
Every household has different needs, and there's no one size fits all in the realm of baby monitors. What matters is that you take the time to understand how different monitors function and how comfortable you are with the security implications of each. To take your home network security a step further, it's a good idea to implement a home antivirus to keep your WiFi and devices secure. When you enable internet access to your baby monitor, it removes many of the typical barriers a hacker would have to penetrate in order to compromise it. Unless you disable remote access, all that stands between a hacker's entry to the monitor is the remote access password you created. To be as secure as possible, it's best to just disable it.
Good VPN routers aren't cheap, setting them up is a hassle, and even the most sophisticated VPN server can be hacked, though is still vastly safer than using port forwarding for this job. You can save public IP addresses by setting up port forwarding. Clients and servers can be protected from unauthorized access, hidden services can be made available on a network, and access from and to a network can be limited. Using port forwarding, the internet application you send from your modem to a specific device connected to the network can be forwarded via ports or port ranges. The internet can be accessed using a WiFi connection or an Ethernet cable if your modem doesn't work.